talk: Increasing Base-Station Anonymity in Wireless Ad-hoc and Sensor Networks, 1:15pm Wed 11/12
UMBC ACM techTalk
Increasing Base-Station Anonymity in
Wireless Ad-hoc and Sensor Networks
Profesor Mohamed Younis
University of Maryland, Baltimore County
1:15pm Wednesday, 12 November 2014, ITE 325b
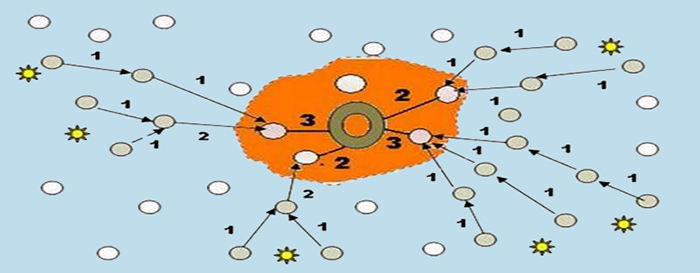
In many applications of ad-hoc networks, the bulk of the traffic is targeted to few nodes. For example, in wireless sensor networks the base-station (BS) collects data from a large number of sensor nodes. Another example is a surveillance network in which the gathered intelligence data about criminal activities flow towards field commanders and/or an in-situ BS. Such a network operation model makes the BS a critical asset for these applications. An adversary can nullify the value of a network by simply disrupting or physically damaging the BS, without targeting individual data sources. The failure of the BS can also cause a loss of important data that may not have been processed and can cause a major negative impact if the BS represents a commanding authority for the network. Therefore, concealing the location and role of the BS is of utmost importance for maintaining a robust network operation.
Packet encryption does not achieve BS anonymity since an adversary can intercept the individual wireless transmissions and employ traffic analysis techniques to follow the data paths without knowing the content of intercepted traffic. Since all active routes end at the BS, the adversary may be able to determine the BS’s location and launch targeted attacks. Similarly, camouflaging or hiding the BS does not provide protection when its location is unveiled via traffic analysis. Employing spread spectrum signaling methods is not a sufficient BS anonymity countermeasure as adversaries are becoming more advanced and equipped with sophisticated intercept technologies. In addition, signal spreading reduces rather than eliminates the prospect of transmission detection. This talk will highlight the traffic analysis threat, present anonymity assessment metrics, provide an overview of effective cross-layer techniques developed in the ESNet Lab for increasing the BS anonymity, and outline open research problems.
Dr. Mohamed Younis is an associate professor in the department of computer science and electrical engineering at the university of Maryland, Baltimore County. He received his Ph.D. degree in computer science from New Jersey Institute of Technology. Before joining UMBC, he was with the Advanced Systems Technology Group, an Aerospace Electronic Systems R&D organization of Honeywell International Inc. While at Honeywell he led multiple projects for building integrated fault tolerant avionics and dependable computing infrastructure. He also participated in the development of the Redundancy Management System, which is a key component of the Vehicle and Mission Computer for NASA-s X-33 space launch vehicle. He has published over 150 technical papers in refereed conferences and journals. Dr. Younis has five granted and two pending patents. In addition, he serves/served on the editorial board of multiple journals and the organizing and technical program committees of numerous conferences. Dr. Younis is a senior member of the IEEE.
Posted: November 11, 2014, 10:59 PM